Create Your First Project
Start adding your projects to your portfolio. Click on "Manage Projects" to get started
Reconnaissance or information gathering
Project Type
Photography
Date
April 2023
It refers to the process of collecting as much information as possible about the target system to find ways to penetrate into the system. This is an important phase and preparatory phase while performing security assessments.
A strong phase of information gathering makes the difference between a good and a bad penetration tester.
A good penetration tester spends 90% of his time widening the attack surface because he knows this is what it is all about. The other 10% is just a matter of launching the correct commands with an appropriate tool with a high success rate.
Subdomain enumeration:-
Subdomain enumeration is the most important part of the reconnaissance phase.
It can help you to widen the scope, this can reveal a lot of sub-domains that are in the scope of security assessment which will provide you more targets to find vulnerabilities and probably increase your chance to get some more good bugs.
For subdomain enumeration, you can choose lots of different strategies and tool
You can go with:-
Subfinder
Assetfinder
Dnsenum
Google Dorking
Dnsdumpster
virustotal
Let’s analyze web technologies:-
Wapplyzer extension — Wappalyzer is a browser extension that uncovers the technologies used on websites. It detects CMS, e-commerce platforms, web servers, frameworks, analytics tool and many more.
Netcraft- It will also allow you to detect back end technologies using by your targets.
Built with- This will let you know that which technology your target is using on their backend.
What web- this is a next-generation web scanner that identifies technologies used by websites. This tool comes preinstalled in your Linux.
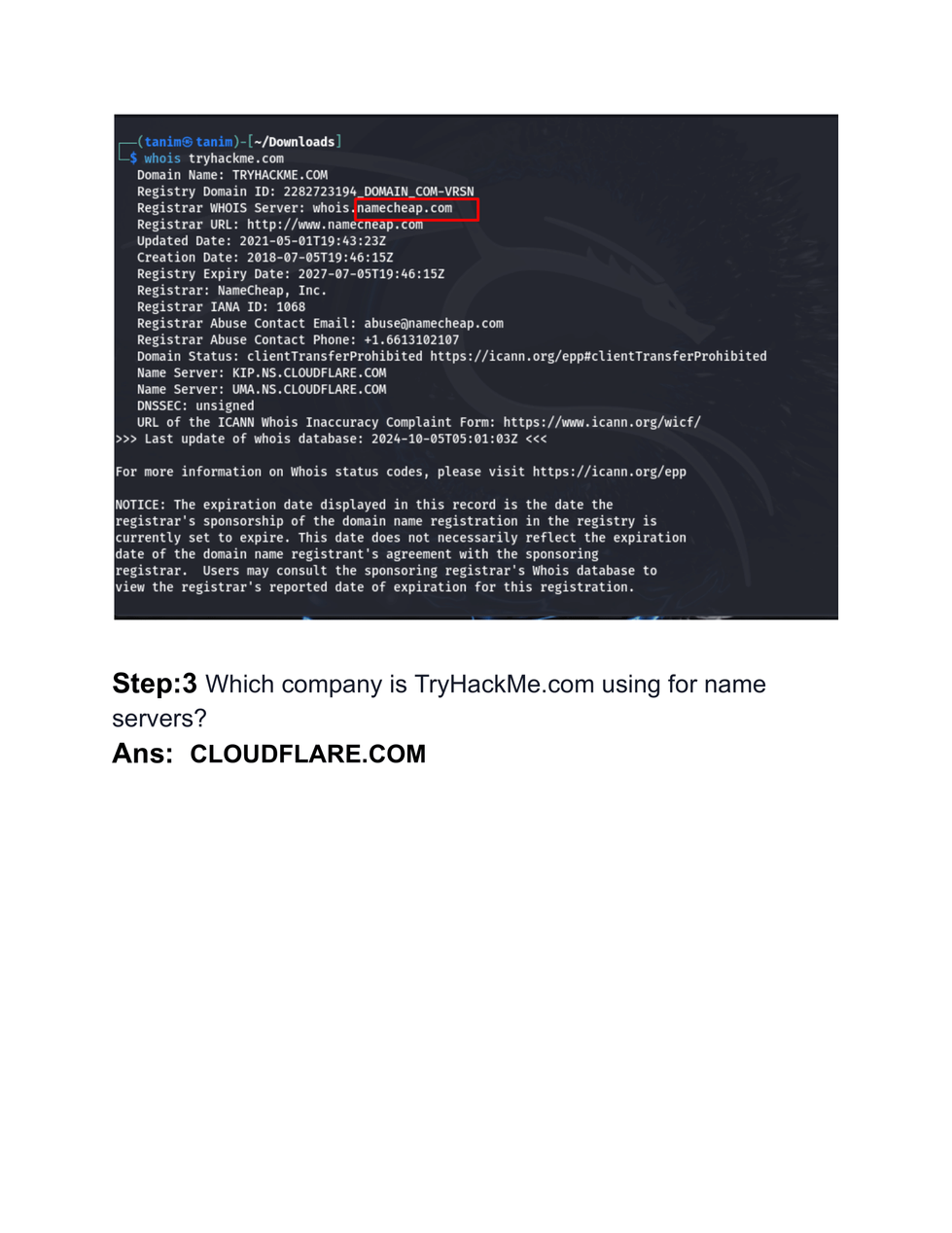
Whois — Search the whois database, look up domain and IP owner information and check out dozens of other statistics.
Network scanning refers to the process of obtaining additional information and performing a more detailed reconnaissance based on the collected information in the foot-printing phase.
To discover live hosts, IP addresses, and open ports of live hosts.
To discover OS and system architecture
To discover services running on hosts
To discover Vulnerabilities running on hosts
Use Nmap(Network mapper )
Nmap is a free and open-source network scanner created by Gordon Lyon. Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection
Let's go with some further information gathering process:-
Google Dorking :-
Google Dorking is the process where we use advanced search operators to make the searching perfect and get focused on the searching topic.